Using Apache JMeter™ to perform load testing for the Azure App Service that requires Azure AD authentication
This tutorial explains how to load testing to Azure App Service with authentication and authorization by Azure AD from Apache JMeter™.
Azure App Service and Azure Functions can be protected by user authentication with Azure Active Directory due to its authentication/authorization feature (Easy Auth).
However, the authentication methods available in the Apache JMeter™ are limited to Basic, Digest, Kerberos and LDAP authentication.
This tutorial explains how to load testing to Azure App Service with authentication and authorization by Azure AD from Apache JMeter™.
Since this content is authorized by access_token, It’s not consider testing for login flow.
Think of it as a test with a login in place.
Advance preparation
There are certain settings that are required for Azure Active Directory to allow access using access_token.
It does not support access by users that require multi-factor authentication.
Turn off multifactor authentication for your test users, or create users that does not require multifactor authentication for testing.
-
Obtaining a client ID of an Azure AD application
Obtain the client ID of the Azure AD application that the App Service is using for authentication.
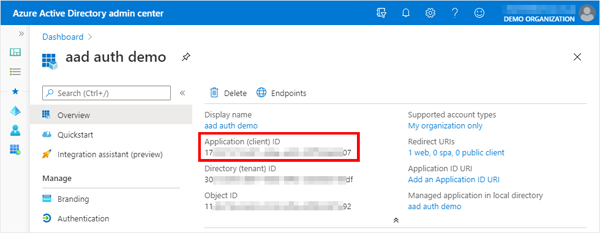
Access the Azure AD Portal(https://aad.portal.azure.com) and select the application that is responsible for the App Service authentication in “App Registrations” and note the “Application (client) ID” value in its “Overview”.
-
Obtaining a client secret of an Azure AD application
Obtain the client secret of the Azure AD application that the App Service is using for authentication.
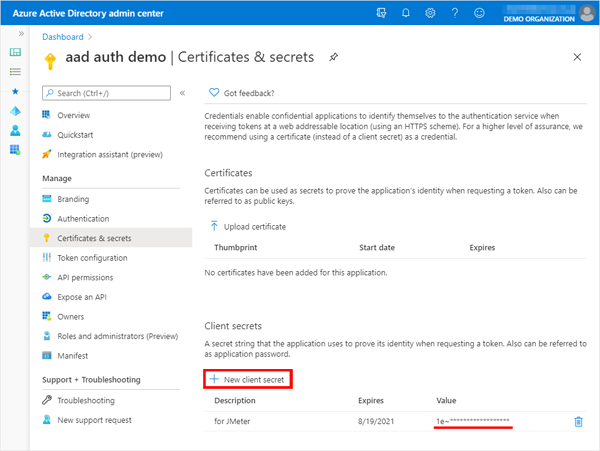
If the client secret is not available for this JMeter test, create a new one.Note that you will not be able to see this value later.
In the application “Certificates & secrets”, add it from “+ New client secret” and note its value.
-
API permissions
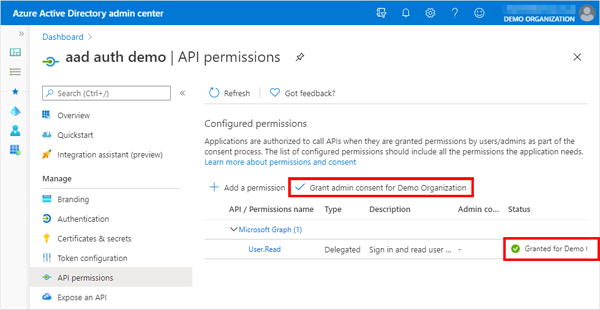
In the “API permissions” of the application, make sure that the administrator’s consent has been granted for “Microsoft Graph > User.Read”.
If not, grant the administrator’s consent through “Grant admin content for {ORGANIZATION}”.
-
Create a list of users and passwords to login
Create a list of users and passwords for test login from JMeter as a CSV file.{USER01}@{DOMAIN}.onmicrosoft.com,{PASSWORD for USER01} {USER02}@{DOMAIN}.onmicrosoft.com,{PASSWORD for USER02} {USER03}@{DOMAIN}.onmicrosoft.com,{PASSWORD for USER03} {USER04}@{DOMAIN}.onmicrosoft.com,{PASSWORD for USER04} {USER05}@{DOMAIN}.onmicrosoft.com,{PASSWORD for USER05} ...Of course, you can also use custom domain account.
-
Install plugin for Microsoft Azure Introduce a function plugin to create an Authorization header to make a request to Cosmos DB.
- Get the plugin
Get the latest plugins (jmeter-plugins-functions-azure-{version}.jar) from the following page using a web browser.
https://github.com/pnopjp/jmeter-plugins/releases - Copy the downloaded jar file to $JMETER_HOME/lib/ext
- Start or restart JMeter
- Get the plugin
Create the test plan
-
Importing a user list from a CSV file
Add “CSV Data Set Config” to the Test Plan, and read the users and passwords from the CSV file you just created.
Add > Config Element > CSV Data Set Config
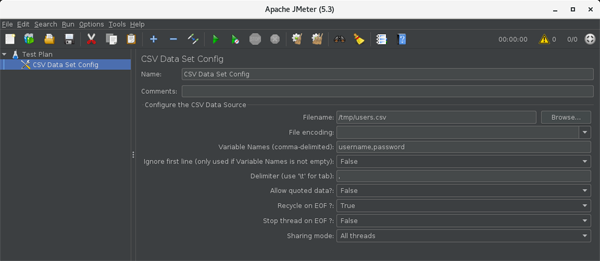
- Filename: CSV file name
- Variable Names (comma-delimited): username,password
-
Define Azure AD application information as variables
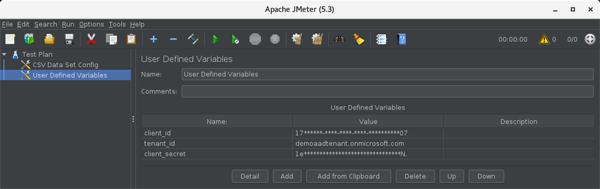
Add “User Defined Variables” to the Test Plan and register the information of the Azure AD application that the App Service uses as authentication.
Add > Config Element > User Defined Variables“User Defined Variables” shows two of the same notation, but probably the upper one.
If you add it, you will see three columns of “Name, Value, Description” in the header of that table.- tenent_id: Domain name of Azure AD (ex. demoaadtenant.onmicrosoft.com, example.com)
- client_id: Client ID of Azure AD application confirmed in advance preparation
- client_secret: Client secret of Azure AD application confirmed in advance preparation
-
Add a Thread Group
Add a “Thread Group” to the Test Plan.
Add > Threads (Users) > Thread Group
Enter the appropriate values for the “Number of Threads (users)” and “Loop Count” to access by different users.
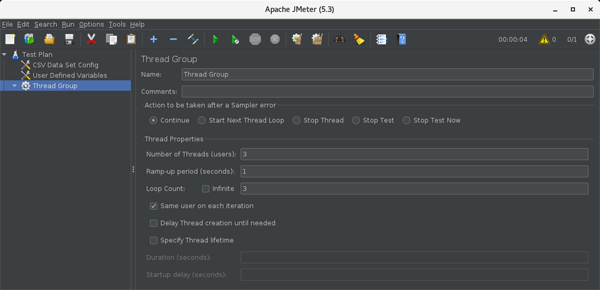
-
Add a HTTP request sampler to access the page after login
Add a “HTTP Request” to the Thread Group.
Add > Sampler > HTTP Request
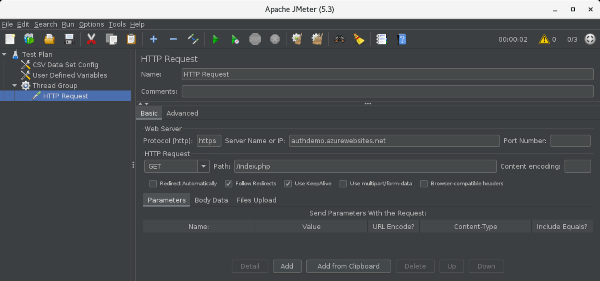
- Web Server
- Protocol [http]: https
- Server Name or IP: Web Apps addresses for load testing with Azure AD authentication (ex. authdemo.azurewebsites.net)
- HTTP Request
- Method: Appropriate value for the request (ex. GET, POST, …)
- Path: Path to authenticated page for target of load testing (A page with login user names and other information will output the login user per access)
- Web Server
-
Add a request header
Add an “HTTP Header Manager” to the added HTTP Request.
Add > Config Element > HTTP Header Manager
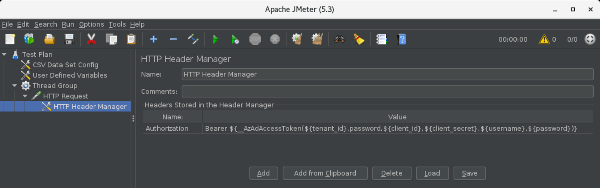
- Headers Stored in the Header Manager
- Authorization: Bearer ${__AzAdAccessToken(${tenant_id},password,${client_id},${client_secret},${username},${password})}
- Headers Stored in the Header Manager
-
Add listeners to see the results of the execution
Add a “View Results Tree” listener to the Test Plan or thread group.
Add > Listener > View Results Tree
Execute it and check the results
Run > Start to run the test and select the resulting “HTTP Request” and then select the “Response headers” tab on the “Response data” tab.
Make sure you get “200 OK” here.
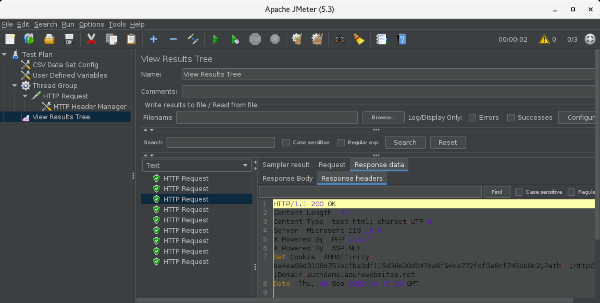
If you’re on a page with a username and other information, you may also want to look at the “Response Body” tab.
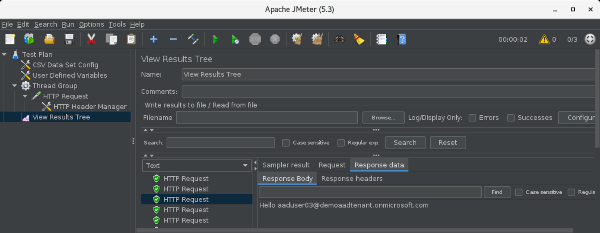
* The Response Body in this image is an example of accessing the following php page.
<?php
echo "Hello " . $_SERVER['LOGON_USER'];
?>
By accessing “https://…/.auth/me”, you can generally get the details of the logged-in user, but in this procedure it seems that it may return an empty value.
Clean up after the load test
Undo any configuration changes you made for testing, such as removing the client secret if you created it in advance, revoking administrative consent if you gave it to the application’s APIs, or removing it if you created a test user.
In this article, I explained how to load testing to Azure App Service with authentication and authorization by Azure AD from Apache JMeter™.
You should be able to load test to Azure Functions with the same settings, so if you’re interested, try it out.